How do I debug a firewall causing connection problems with my Droplet?
If a host-based firewall on your Droplet is misconfigured, it can prevent connections to or from your computer. Misconfigured DigitalOcean cloud firewalls can also cause network problems. If your setup uses both firewalls, they may have conflicting rule sets.
Debug your Droplet Firewall
You can check to see if any firewall rules are active on your Droplet before troubleshooting them further using IPTables. IPTables is a utility program that manages firewalls and is native to all Linux operating systems.
To see if you have any firewall rules in place on your Droplet, run:
iptables -L
If the command returns the following output, the Droplet does not have any active filtering rules, and you do not need to debug them further. Instead, check your cloud firewall settings
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
If the command returns longer output with policies set to DROP, the Droplet’s firewall is active. In the sample output below, IPTables returned firewall policies that are set to only accept TCP traffic on port 2222 and were configured using UFW.
Chain INPUT (policy DROP)
target prot opt source destination
ufw-before-logging-input all -- anywhere anywhere
ufw-before-input all -- anywhere anywhere
ufw-after-input all -- anywhere anywhere
ufw-after-logging-input all -- anywhere anywhere
ufw-reject-input all -- anywhere anywhere
ufw-track-input all -- anywhere anywhere
...
Chain ufw-user-input (1 references)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere tcp dpt:2222
If the Droplet has active firewall policies, use one of the following tools to review the firewall rules on the Droplet. We recommend using UFW to manage your firewall rules as it is the most user-friendly firewall interface.
UFW is an interface for managing netfilter firewall rules and all Ubuntu Droplets have UFW installed by default. You can view the current filtering rules by running:
sudo ufw status verbose
Adding the verbose argument returns a more detailed status of the firewall.
If you receive the message Status: inactive, UFW is not currently configured to manage your firewall and you can try reviewing your Droplet’s firewall settings with iptables. If UFW is currently active, it returns output similar to the following:
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp (OpenSSH) ALLOW IN Anywhere
22/tcp (OpenSSH (v6)) ALLOW IN Anywhere (v6)
The output displays a few things:
Status: Indicates that the firewall is actively enforcing traffic rules.Default: Indicates the current incoming and outgoing traffic policies. The provided example shows that the incoming policy is to deny connections to the Droplet from outside sources, and the outgoing policy allows traffic from the Droplet to connect to the public internet.- The rule set at the bottom indicates the types of traffic that are allowed to connect to and egress from the Droplet. In the example, the rule set allows incoming connections to port 22 from both IPv4 and IPv6 addresses. Because all outbound traffic is allowed to egress from the Droplet, no outbound rules are displayed in the rule set.
If you have a DigitalOcean Cloud Firewall set up with conflicting rules, you can disable your UFW firewall by typing:
sudo ufw disable
If you want to keep your Droplet’s firewall in place to filter types of traffic not covered by DigitalOcean’s Cloud Firewall service, such as SFTP traffic, you should modify its rules to match the cloud firewall settings to ensure there are no conflicting rules between the two firewalls. You can learn how to modify the UFW rules by following the UFW Essentials: Common Firewall Rules and Commands guide.
FirewallD is an interface for managing a netfilter firewall designed to be user friendly. It is available for most Linux operating systems. If your Droplet runs FirewallD, you can view the current traffic rules with a sequence of checks.
First, check whether FirewallD is active using the --state flag:
sudo firewall-cmd --state
If you receive the message running, check the active zones using the --get-active-zones flag:
sudo firewall-cmd --get-active-zones
The command returns any network interfaces FirewallD actively controlled by FirewallD rules.
public
interfaces: eth0
If FirewallD has active zones, it means that it is evaluating traffic against a set of rules. In the example output, FirewallD is currently managing traffic for the Droplet’s eth0 network interface.
You can display the ports and services associated with each of the active zones with the --info-zone option:
sudo firewall-cmd --info-zone=public
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
sourceports:
icmp-blocks:
rich rules:
Check whether any ports are open by looking at:
- The
targetvalue. If this is set toDROPor%%REJECT%%, the Droplet denies all traffic regardless of the other settings. - The
portsvalue. This lists ports explicitly allowed through the firewall. - The
servicesvalue. This lists services that are allowed through the firewall. In the example output above, thedhcpv6-clientandsshservices are allowed through the firewall.
You can also check the ports associated with these services by typing:
sudo firewall-cmd --permanent --get-ports --service=dhcpv6-client
sudo firewall-cmd --permanent --get-ports --service=ssh
The example commands return the ports and network protocols associated with the services.
546/udp
22/tcp
If you have a DigitalOcean Cloud Firewall set up with conflicting rules, you can disable your firewall via FirewallD by typing:
sudo systemctl stop firewalld
sudo systemctl disable firewalld
If you want to keep your Droplet’s firewall in place to filter types of traffic not covered by DigitalOcean’s Cloud Firewall service, such as SFTP traffic, you should modify its rules to match the cloud firewall settings to ensure there are no conflicting rules between the two firewalls. You can learn how to modify the FirewallD rules by following the How To Set Up a Firewall Using FirewallD on CentOS 7 guide.
IPTables is a utility program that manages firewalls on Linux systems. It’s native to all Linux operating systems. If you are using IPTables to manage the Droplet’s firewall, you can view the current IPv4 filtering rules by typing:
sudo iptables --line-numbers -vL
The --line-numbers flag prepends a num column to the output to make the returned chart more human-readable. The -vl flag returns verbose output.
Chain INPUT (policy DROP 1 packets, 40 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
2 764 56512 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
3 9 540 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
4 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 374 packets, 97673 bytes)
num pkts bytes target prot opt in out source destination
The output indicates:
- The default
policyfor incoming and outgoing traffic (DROPfor incoming, andACCEPTfor outgoing). - The exceptions to the default policies. In the example output above, the policy contains exemptions for incoming TCP traffic to ports
22and80.
The iptables command only displays the rules for filtering IPv4 traffic. To show the IPv6 filtering rules, rerun the command using the ip6tables command instead of iptables.
If your cloud firewall has rules that conflict with your iptables firewall, you can disable your iptables firewall by running:
sudo iptables -P INPUT ACCEPT
sudo iptables -P OUTPUT ACCEPT
sudo iptables -P FORWARD ACCEPT
sudo iptables -F
sudo ip6tables -P INPUT ACCEPT
sudo ip6tables -P OUTPUT ACCEPT
sudo ip6tables -P FORWARD ACCEPT
sudo ip6tables -F
If you are using a service like iptables-persistent or have a script loading iptables rules at boot, you may have to disable them to disable the firewall.
If you want to keep your Droplet’s firewall in place to filter types of traffic not covered by DigitalOcean’s Cloud Firewall service, such as SFTP traffic, you should modify its rules to match the cloud firewall settings to ensure there are no conflicting rules between the two firewalls. You can learn how to modify the iptables rules by following the Iptables Essentials: Common Firewall Rules and Commands guide.
Debug your Cloud Firewall
To check your firewall settings from the control panel, click Networking, then click the Firewalls tab. The page lists the firewalls set up in your account.
Click the firewall protecting your Droplet and review your firewall’s rules.
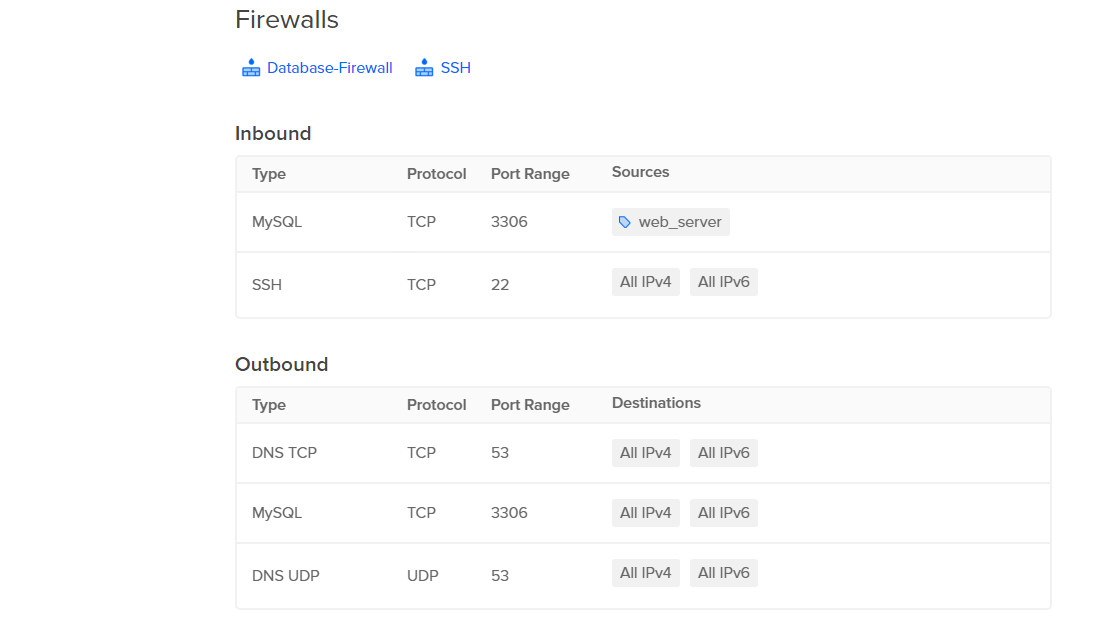
The Inbound Rules section displays the types of traffic that are allowed to reach your Droplet. The firewall blocks any traffic from sources not explicitly listed in the inbound rules. For example, if your Droplet is linked to a firewall in your account and the firewall’s inbound rules do not list an SSH rule, the firewall blocks any attempts to connect via SSH.
The same concept applies to the firewall’s Outbound Rules, the firewall blocks any traffic from the Droplet not explicitly listed in the outbound rules.
If you can’t reach your Droplet via a specific connection type or you can’t reach the internet from your Droplet via specific connection type, configure a firewall rule allowing that type of traffic to reach or exit the Droplet.